The automated pentesting sequence
that works in the background so you don’t have to.
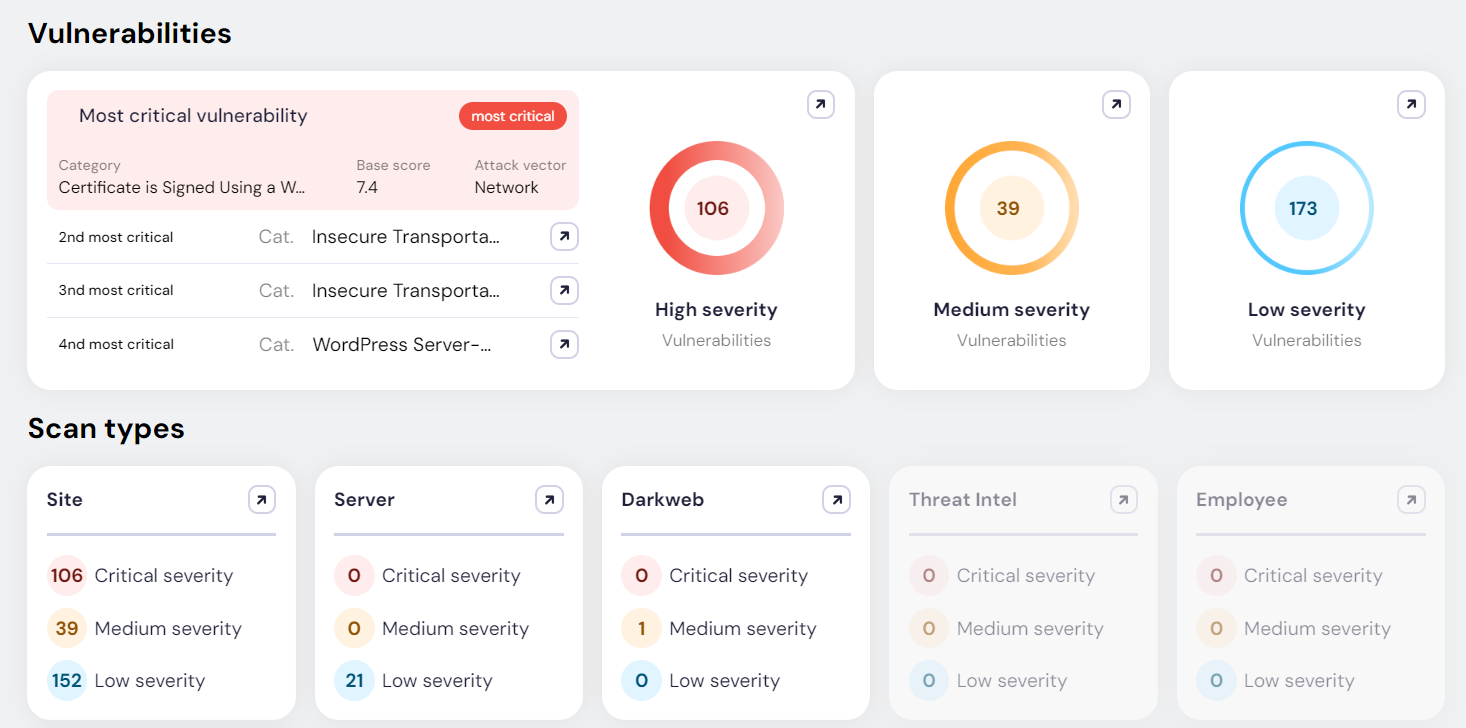
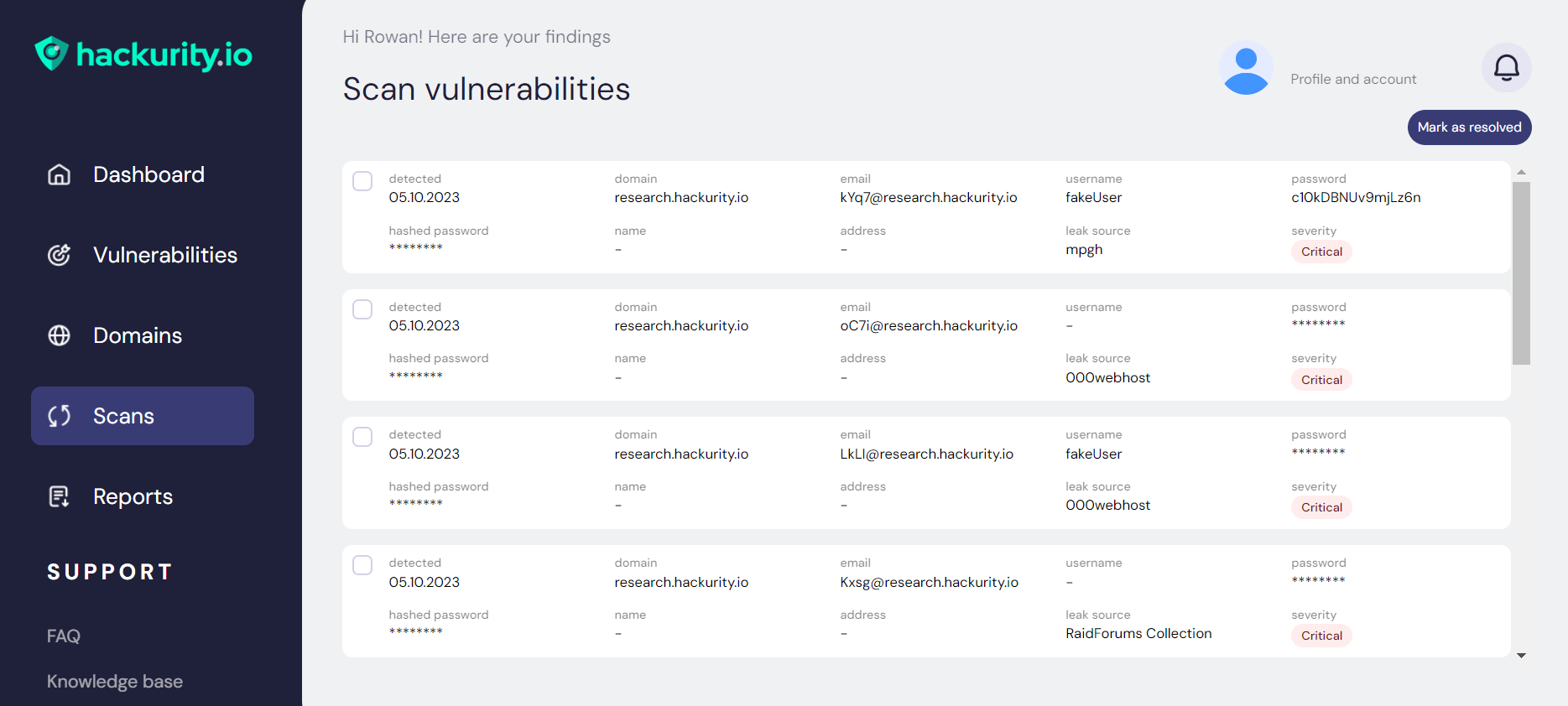
Our flagship black box scanning solution identifies vulnerabilities within your entire attack surface:
external IPs, web apps, APIs and EUDs.
This is where most vulnerability scanning solutions stop.
By chaining results and automating the use of refined open source exploit vectors, Atrax exploits any discovery with payload-less attacks.