Secure by Nature.
Human by Design.
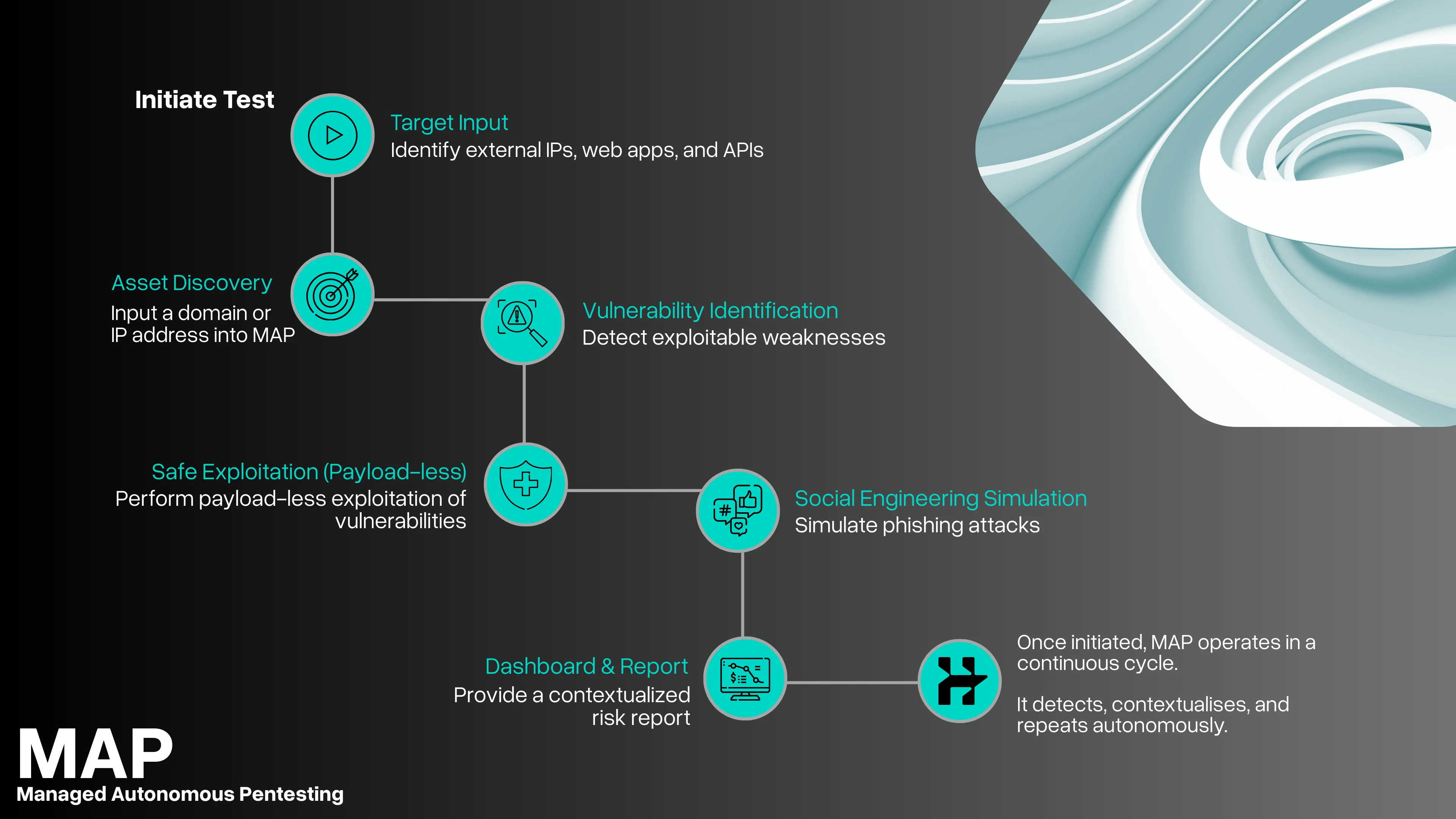
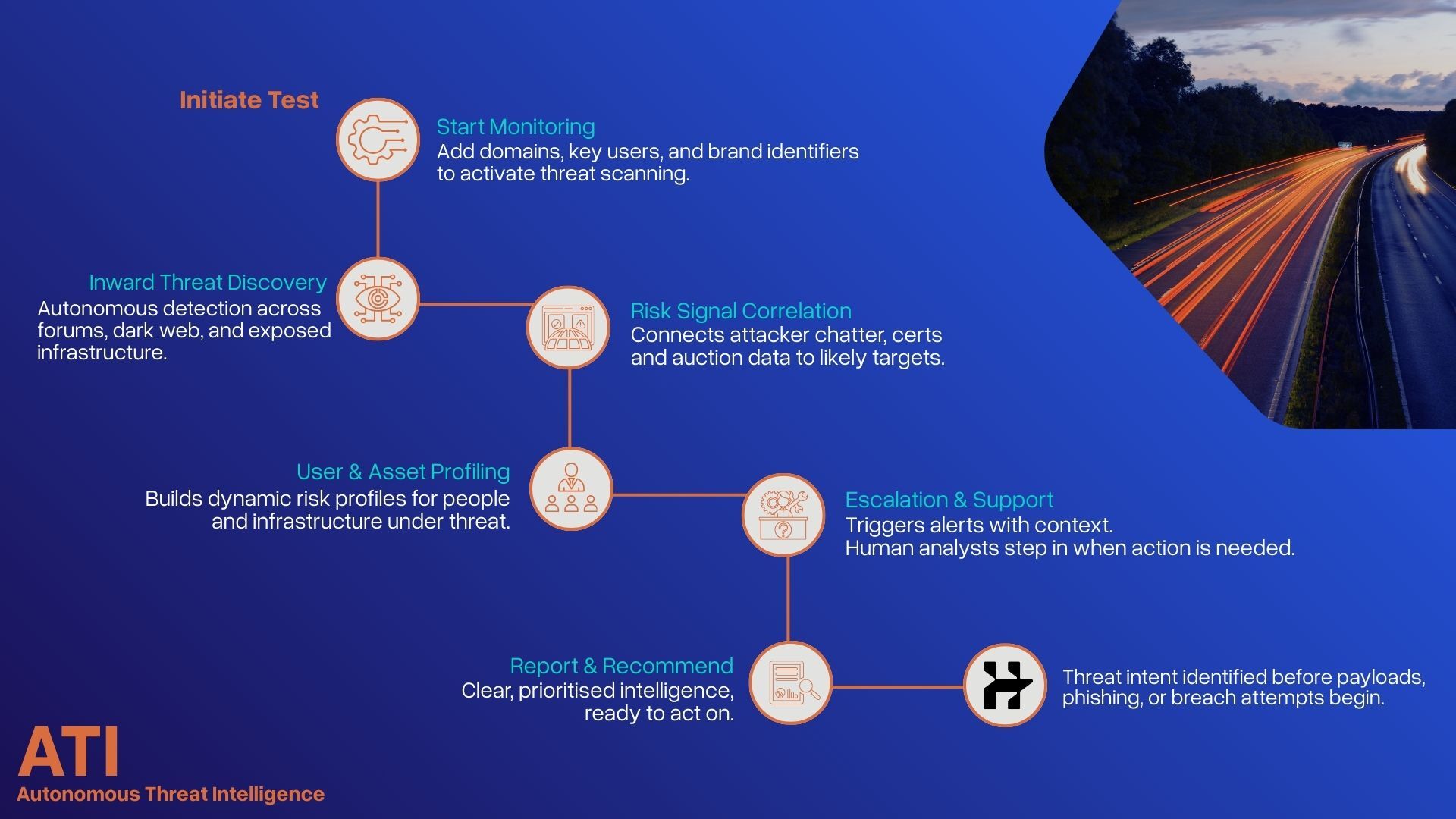
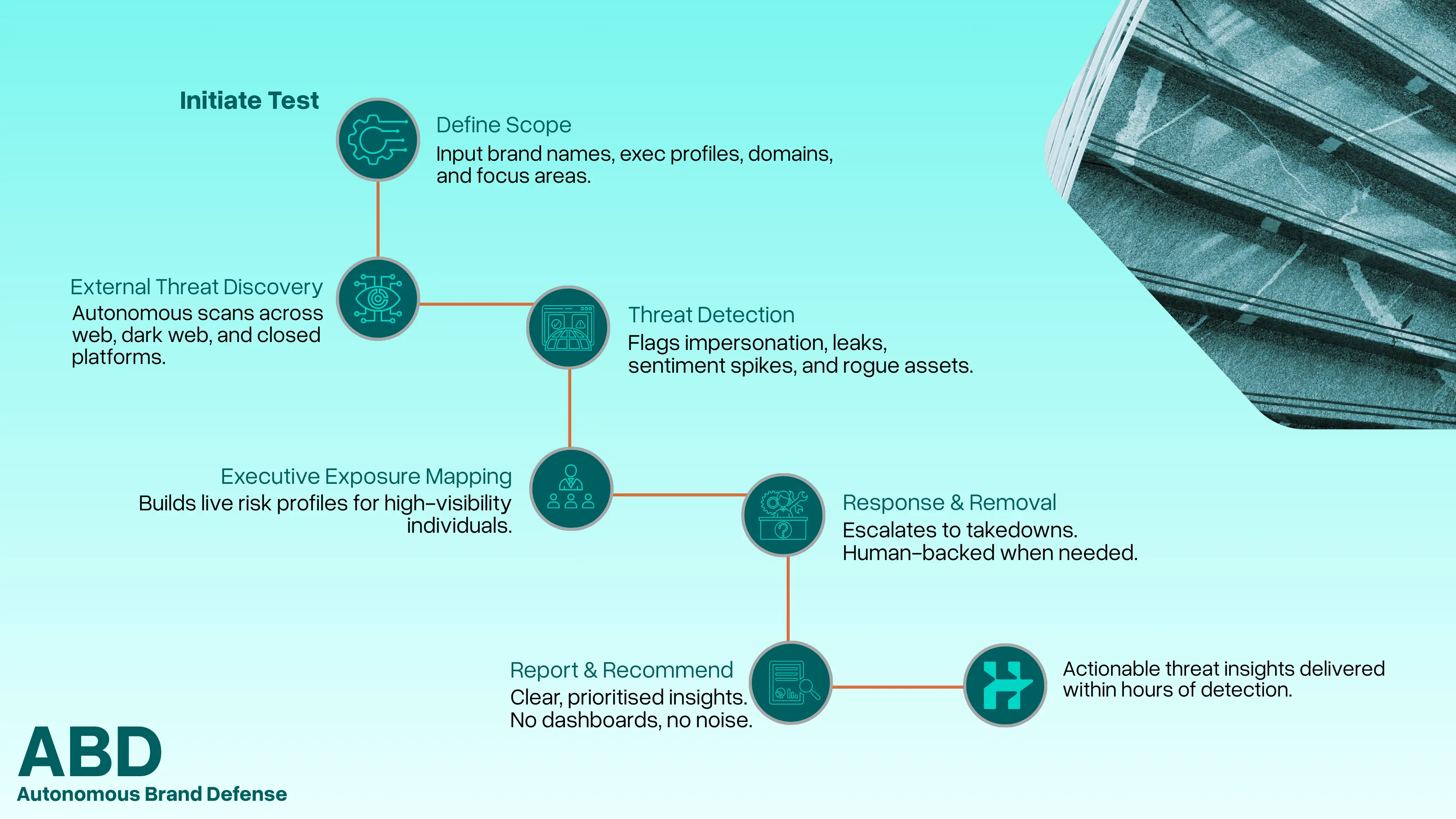
Real attacker behaviour. Simulated safely, explained clearly. Autonomous Red Teaming (ART) backed by experts who stay involved, prioritise what matters, and help you fix what attackers would target.