Our Autonomous Red Teaming Stack (ART)
Attack-surface exposure, mapped and validated
Managed Autonomous Pentesting
Autonomous red teaming that runs continuously in the background, without disrupting your environment.
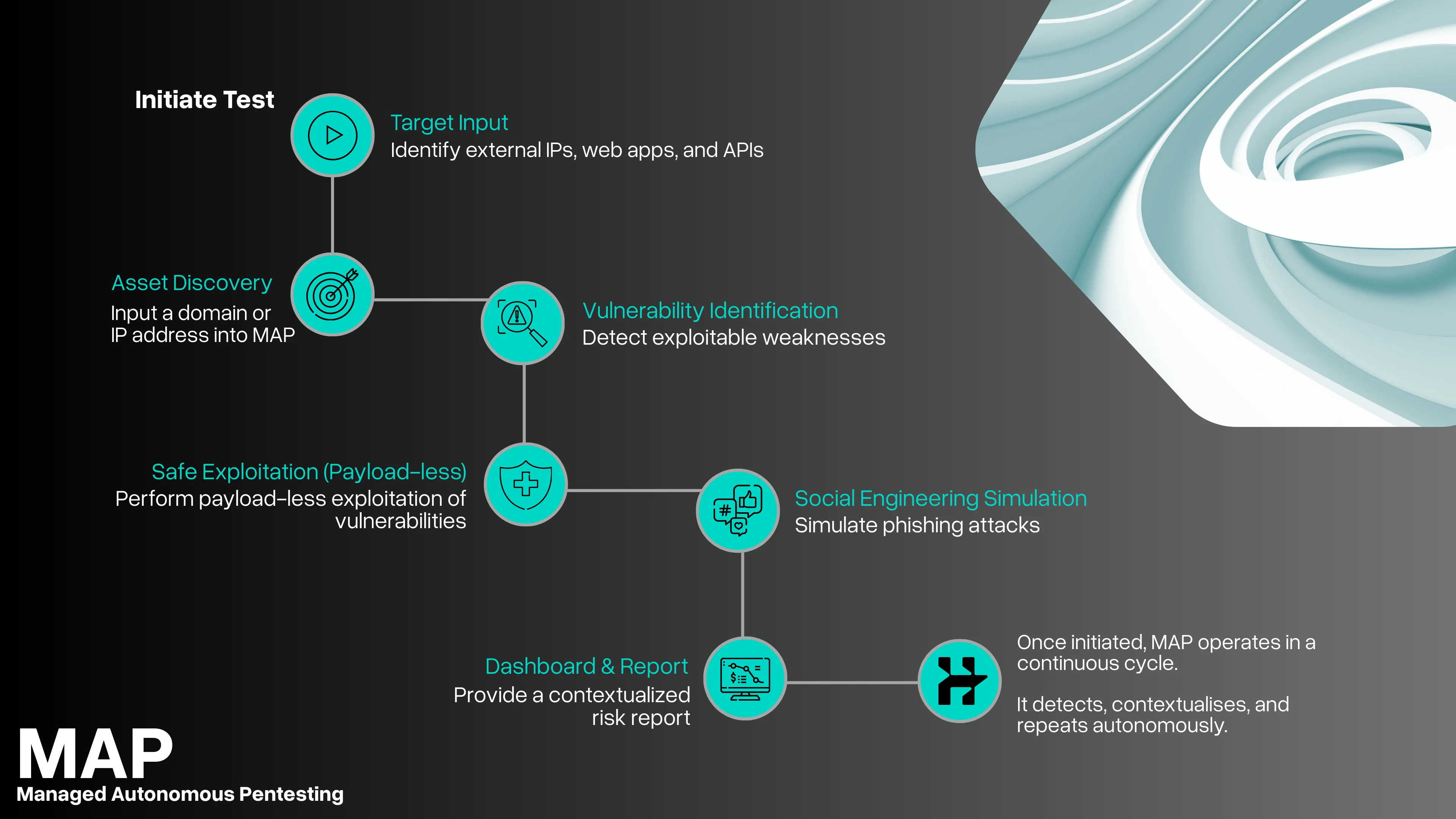
MAP safely simulates real-world attacks across your external IPs, web applications, APIs, and endpoints. Instead of stopping at discovery, it chains findings together to validate real attack paths using payload-less exploitation.
Each exploit is strictly constrained to the specific vulnerability being tested, ensuring impact is proven without putting production systems at risk.
Using the same architecture, MAP evaluates trust boundaries introduced through third-party software and updates, exposing how supply chain access could be abused in practice.
The result is not a list of issues, but a clear picture of how an attacker would move through your environment, what they would reach, and why it matters.
I Want To Know More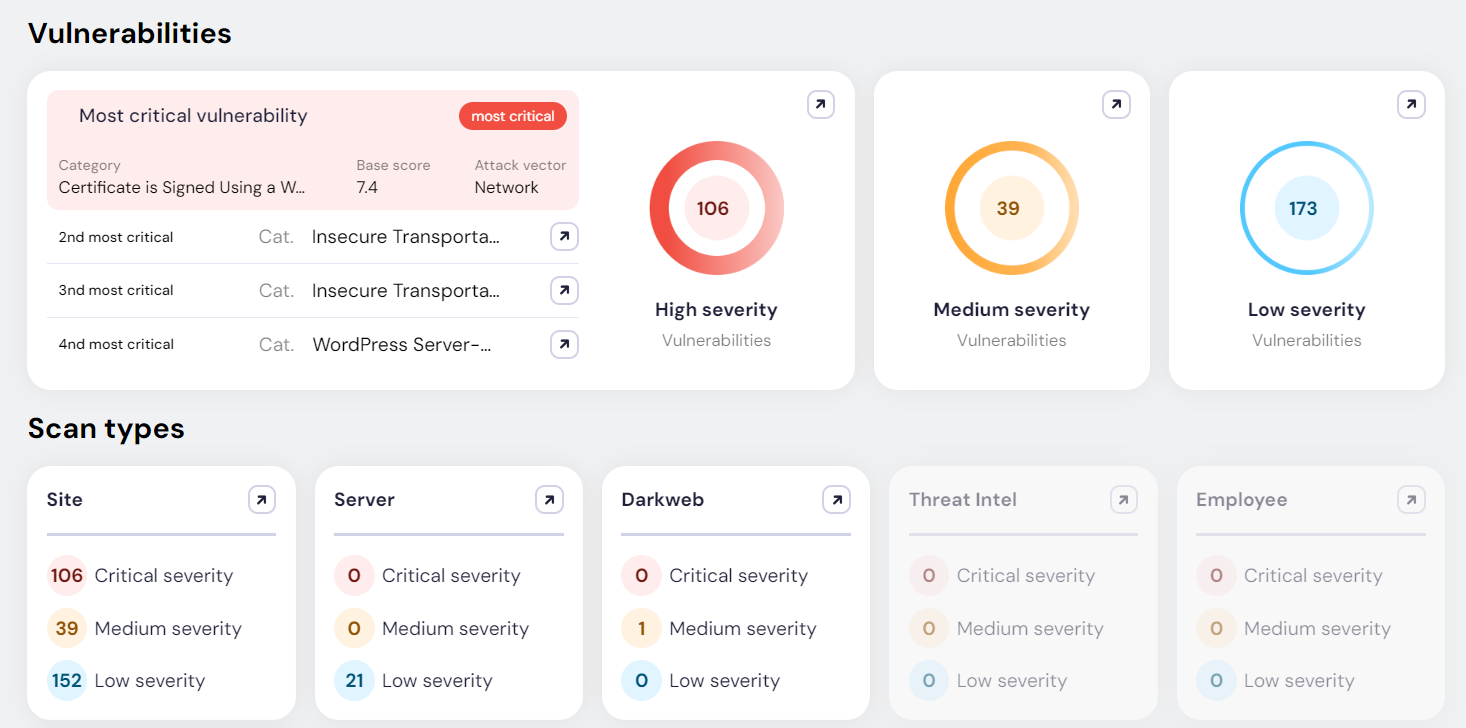
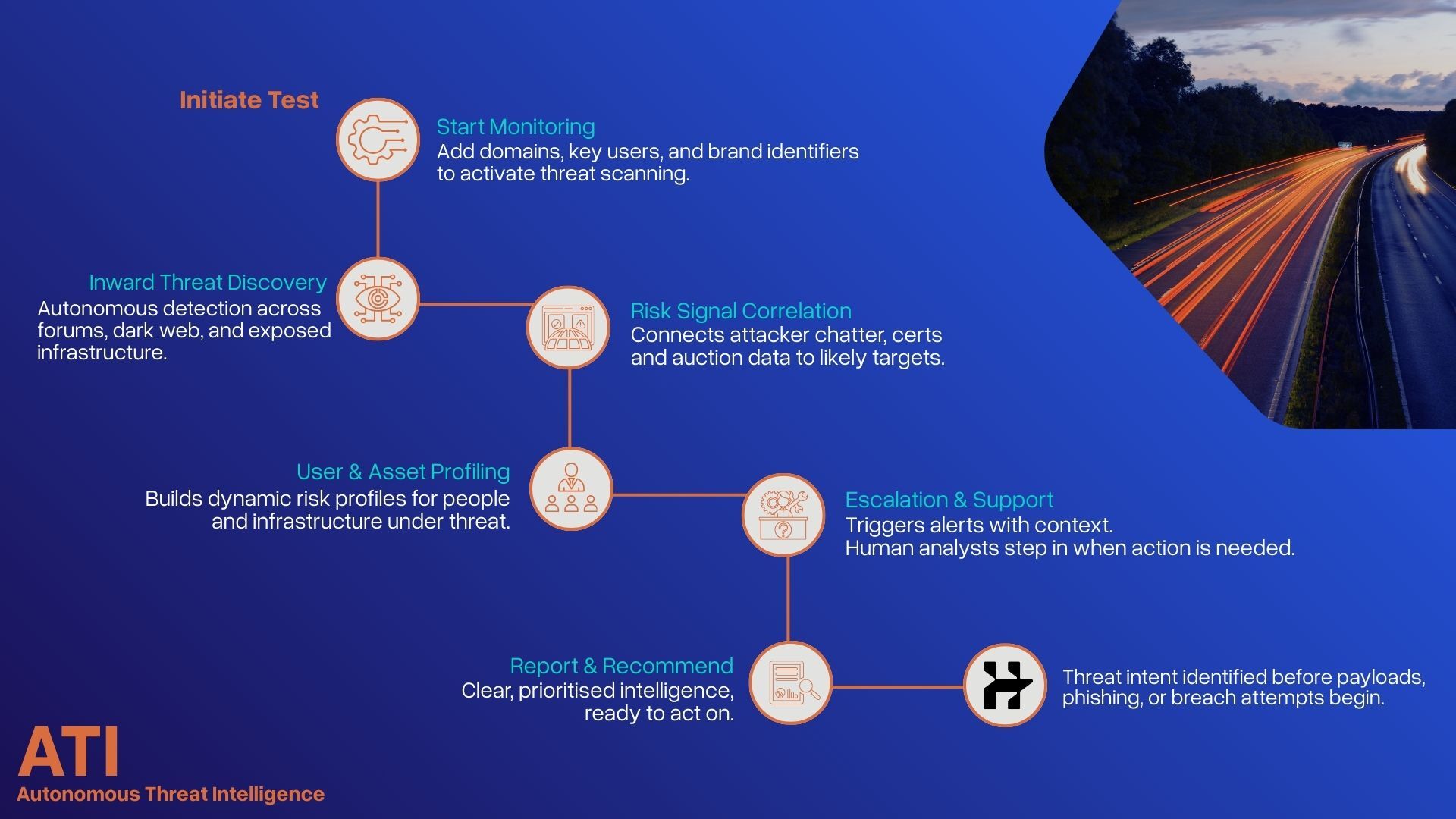
Autonomous Threat Intelligence
Attacker-focused intelligence that shows when preparation is happening, not after damage is done.
ATI goes beyond forum-based dark web scanning. It correlates data from breach dumps, underground marketplaces, infrastructure scans, certificate transparency logs, and grey-noise chatter to build attacker-relevant risk profiles.
This intelligence is used to understand who is being targeted, how impersonation could happen, and which identities or access points attackers would abuse first.
By analysing domain ownership patterns, certificate behaviour, hosting infrastructure, and historical associations with known threat actors, ATI surfaces impersonation and trust-abuse risks before they are operationalised.
This is not alerting or monitoring. It is adversary preparation visibility, designed to support red team simulation and prioritisation.
I Want To Know More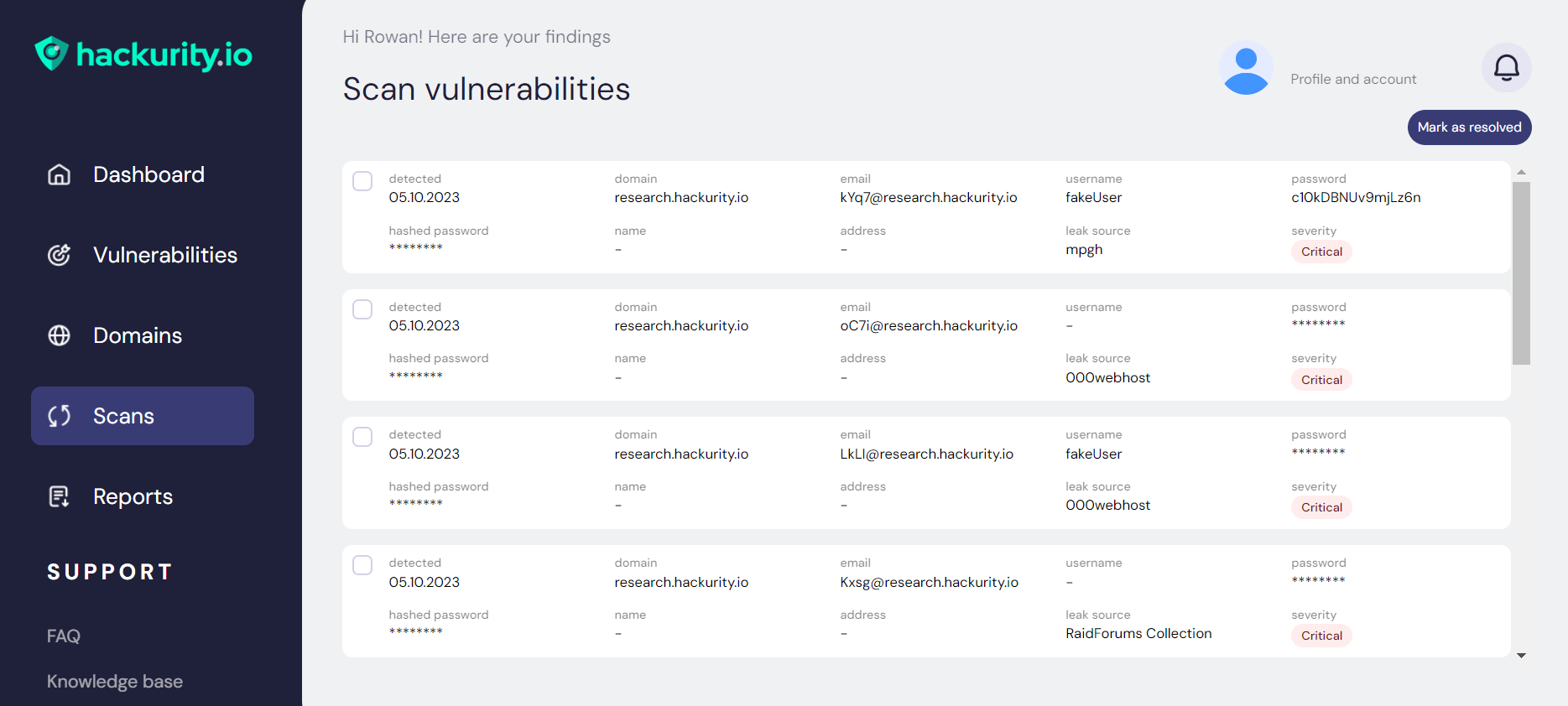
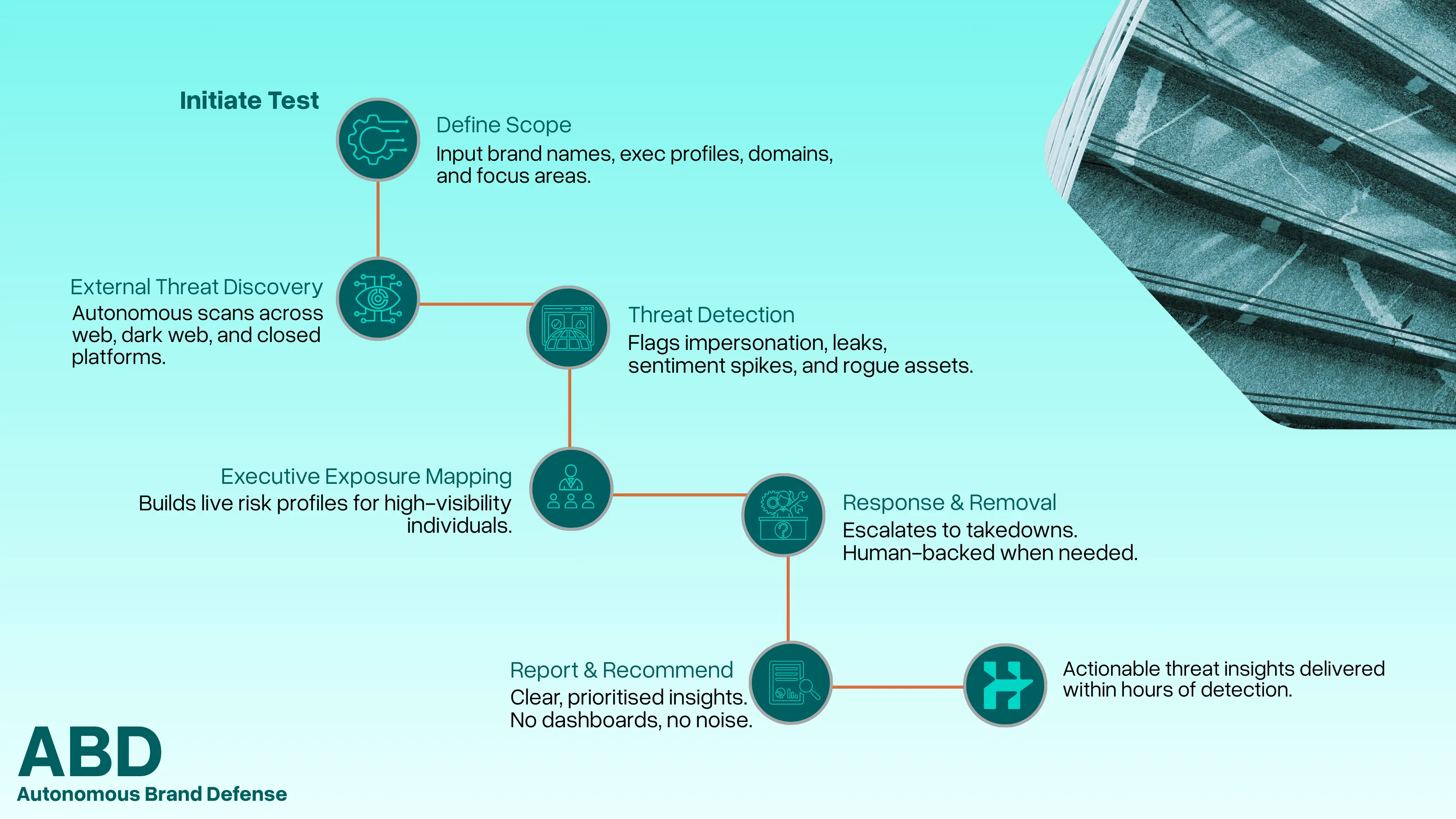
Autonomous Brand Defence
External attack surface monitoring focused on brand abuse and impersonation.
ABD continuously identifies domains, services, and communications that attempt to impersonate your organisation, products, or leadership. This includes phishing infrastructure, fake services, and brand abuse across the open web and messaging platforms.
Once identified, Hackurity coordinates takedown and mitigation workflows to remove active threats before they reach users.
ABD focuses on stopping abuse of trust, not on managing reputation or sentiment. It exists to remove attacker-controlled assets that exploit your brand to gain access.
I Want To Know More