
Globally, the cyber security market is booming. Experts at Gartner predict that end-user spending for IT security and risk management will increase from $ 172.5 billion in 2022 to $ 267.3 billion in 2026.
A major area of spending includes the art of testing cyber security defences, better known as (cyber) security testing. MarketsandMarkets forecast the global penetration testing market size to grow at a compound annual growth rate (CAGR) of 13.7% from 2022 to 2027. However, there are two main things that are hindering the market growth. Firstly, the costs of penetration testing are high and quality, in-depth pen tests can easily cost an organisation somewhere upwards of $10,000. Secondly, pen tests have their limitations. Something you can also read in our previous blog. For those reasons many cyber security professionals are moving towards an alternative solution.
Pen tests do not solve cyber security pain points
Pen testing serve important and specific purposes for organisation. For many organisations it serves the purpose of compliance. However, pen testing isn’t always the best fit for the following cases.
- Your IT infrastructure and environments change continuously
Securing an IT infrastructure which is constantly changing and faces evolving external threats is an extremely difficult challenge. Pen testing focuses on one moment in time and therefore the result won’t always be the same after the next change you make within your infrastructure. In short, pen testing is a snapshot.
2. Your organisation is growing rapidly
Leaders of scale up businesses will agree, every fast growing organisation experiences growing pains. CISOs face the challenge of maintaining visibility of their organisation’s rapidly expanding attack surface.
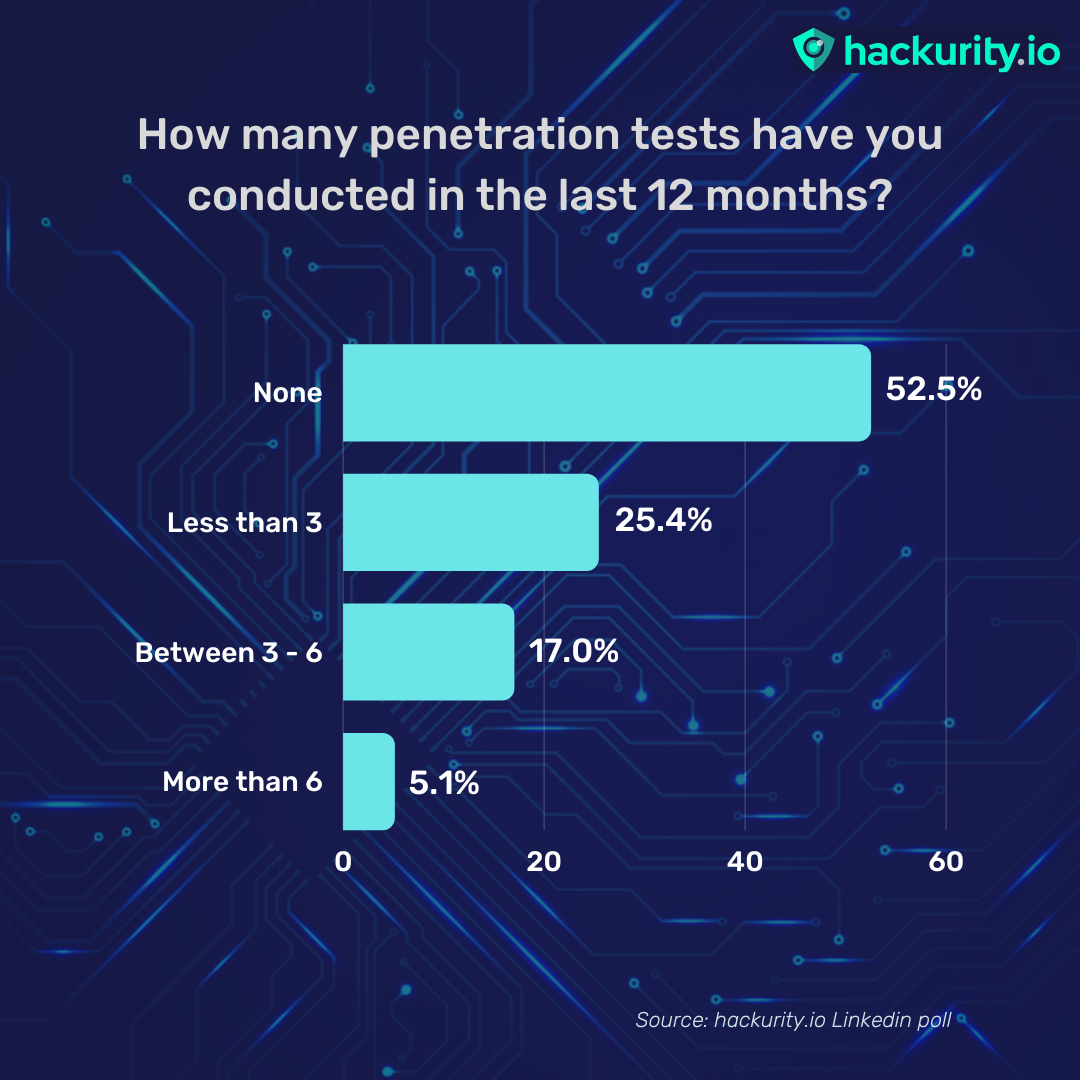
Our LinkedIn poll shows that 25% of respondents conduct less than 3 pen tests per year and a staggering 52% haven’t done any in the last twelve months. This is woefully insufficient given how quickly infrastructure and applications change.
3. Shortage in cyber security skills
Budget constraints are not the only challenge. The ability to find the right skillset for internal cyber security staff is an uphill battle. This can result in organisations failing to spot and remediate promptly and adequately security vulnerabilities.
External pen testers can provide a great outside in perspective. However, often it is just a single pen tester performing the test. On top of that, it is hard to trust the result of the work of a single or even two pen testers. Not every pen tester is equal, it’s near impossible to determine their ability beforehand.
Additionally, there are unfortunately also larger non-cyber security specialised consultancy firms who understand pen testing often is required for compliance. Therefore, the skillset of their pen testers is sufficient, but not extraordinary. As a result vulnerabilities may be left unexposed and available for threat actors to exploit.
4. Rapid evolving cyber threats
Unfortunately for the good guys, cyber criminals keep evolving their attack tactics and constantly developing new tools, techniques and strategies for cyber attacks on organisations. For CISOs and their teams it’s a near impossible task to stay up to date with the latest cyber attack techniques and tactics. Of course it’s also impossible for organisations to hire new, specialist staff for every specific cyber threat.
HelpNetSecurity reported that it takes 71% of pen testers anywhere from a week to a month to conduct a full in-depth pen test. After completion, 26% of organisations must wait between one to two weeks to get the results. Considering the speed with which cyber threats evolve, this waiting period can leave organisations exposed to potential security issues.
5. Pen tests don’t keep up within agile environments
Continuous development lifecycles outpace pen testing cycles. Development of IT infrastructure and applications are rolled out frequently and mistakenly can create vulnerabilities during large security testing gaps. In that case, vulnerabilities remain undiscovered for some time.
Redefining cyber security and security testing
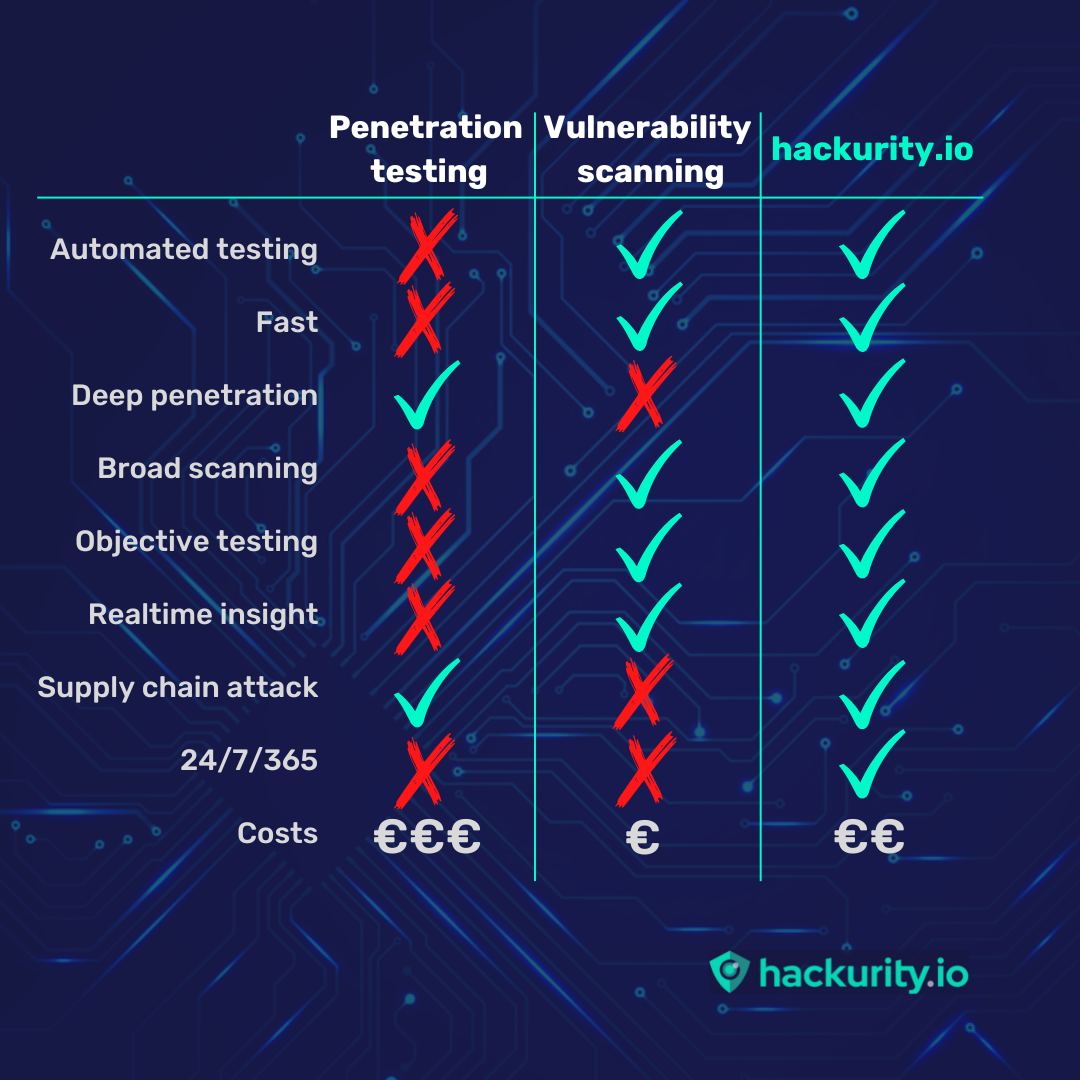
At hackurity.io we understand the requirement for continuous security testing. That’s why we have accumulated our years of experience to develop security testing solutions that provide organisations with continuous, 24/7/365, security testing. This creates a redefining realtime insight in an organisation’s cyber security defence. How do we do that?
The HIO Engine
HIO Engine is our innovative and all-in-one infrastructure vulnerability scanner and penetration testing solution. HIO Engine is unique, because it effectively combines penetration testing and infrastructure vulnerability scanning in a fully automated process allowing it to run 24/7/365.
Through HIO Engine, we replicate the process of a real threat actor or hacker and take the outside in approach. We do not require login details, internal agents or any other type of initial network access for our solution to work. We also aim to achieve consistency by planting reverse shell triggers and/or backdoors as part of our network enumeration.
HIO Engine scans your domain automatically and continuously. Once HIO Engine finds vulnerabilities it will take two actions.
1. It will, within minutes, automatically notify you of the most critical vulnerability found through email. This email contains CVE number, description and fix.
2. It will actively exploit the vulnerability and progress in penetrating your IT infrastructure.
In addition to its ability to scan and penetrate your IT infrastructure, HIO Engine has more tools in its toolbox, like the ability to bypass firewalls. It also is able to conduct supply chain attacks on your IT solution providers, i.e. your domain host. Like real threat actors HIO Engine will apply various techniques and tactics in order to penetrate your IT infrastructure.
Technically HIO Engine runs as a lambda and it's in a constant recursive loop; first enumerating the given target, then trying to attack it based on the resulting information. If it succeeds it then goes back to enumerating using the newly gained access or information. This loop goes on until a viable compromise vector is found. Depending on the size of the loop this can be one or more vulnerabilities chained together.
We differentiate VulPen Engine further by aggregating several vulnerability databases, as well as adversary simulation frameworks. This in effect ensures that we can target our customers with new CVEs as soon as they get their attack vector or exploit POC assigned. This is weeks before the public media or news sites pick up the new CVEs, which happens only after a high profile target is compromised.
About hackurity.io
Hackurity.io is redefining cyber security through our innovative, automated and powerful cyber security and attack simulation tools. Taking a unique outside in approach, our solutions are designed to replicate real hacker attacks to find and fix vulnerabilities before hackers do. Focused on prevention, we reduce the chance of a successful cyber attack on any business by up to 95%
Founded in 2021, hackurity.io has the dream and mission to make being connected to the internet safer for all businesses and ultimately for our next generations. Headquartered in The Netherlands, hackurity.io offers its world class cyber security solutions to businesses around the world.