
The conventional method of penetration testing is under scrutiny: is it past its prime? Penetration testers have long served as the vanguard of offensive teams, leveraging their expertise to uncover vulnerabilities, misconfigurations, and architectural flaws. While this role has been invaluable, the rapidly evolving landscape of modern threats calls for a fresh perspective.
Benefits of penetration testing
Penetration testing, a cornerstone of contemporary cybersecurity strategies, provides a comprehensive approach to bolstering organisational defences against ever-changing threats. By conducting thorough examinations of network infrastructure, applications, and external assets, penetration testing acts as a proactive measure to detect vulnerabilities before they can be exploited.
Uncover Weaknesses: Unearth vulnerabilities across your infrastructure, spanning internal networks, applications, and external assets, to preclude potential exploits.
- Minimise Risks: Reduce the likelihood of security breaches, operational disruptions, and financial harm through thorough testing, integrated security checks, and streamlined resolution procedures.
- Enhance Defence: Proactively strengthen your security stance by addressing potential entry points for adversaries, both within and beyond your network. Benefit from expert guidance for remediation and undergo retesting for up to 12 months.
- Ensure Regulatory Compliance: Meet industry regulations and standards by consistently evaluating and enhancing your network security. Customised reports include attestation letters and succinct summaries for stakeholders.
Yet, confronted with constantly expanding and swiftly evolving attack vectors, organisations frequently encounter limitations in the effectiveness of traditional penetration testing. Compounding this challenge is the breakneck pace of exploit development.
Embracing offensive cybersecurity, which entails scrutinising security from the perspective of a genuine threat actor, is paramount. This approach aids in pinpointing vulnerabilities in cybersecurity and assessing exposure posture. Offensive security encompasses three crucial dimensions:
- Precision and comprehensiveness of assessments
- Regularity and breadth of scanning
- Adaptability and total cost of ownership
Navigating the Pitfalls of Penetration Testing
In the perpetual game of cat-and-mouse between defenders and adversaries, the pressing need for adaptive and proactive cybersecurity measures becomes increasingly evident, aiming to effectively mitigate risks and safeguard your assets.
Penetration testers are intimately acquainted with the complexities of identifying, prioritising, and managing vulnerabilities across a diverse range of assets. The statistics paint a stark picture:
- 69% of organisations have fallen victim to attacks targeting poorly managed external-facing assets.
- 68% of all cyberattacks exploit vulnerabilities for which a patch has been available for over a year.
- 86% of codebases harbour at least one vulnerability, with 48% containing a high-risk vulnerability.
- 52% of organisations are contemplating a switch to new assessment solutions to curb false positive alerts.
- 66% of security teams grapple with the challenge of safeguarding intricate and dynamically evolving attack surfaces.
Addressing the Escalating Demand for Continuous Threat Exposure Management
In the current cybersecurity landscape, attackers pivot rapidly, often leaving organisations racing to automate controls and deploy security patches in a bid to keep pace. However, such reactive measures do little to diminish future exposure. Research underscores the importance of continuous threat exposure management (CTEM) as a proactive program that identifies and prioritises threats most pertinent to businesses.
CTEM operates across various domains, optimising workflows to bolster the cybersecurity posture of organisations. By 2026, organisations prioritising their security investments based on a continuous exposure management program are projected to be three times less susceptible to breaches.
Analysing the Gap in Legacy Tools
Once effective, legacy penetration testing tools now encounter significant hurdles in keeping pace with the ever-evolving threat landscape. Traditional tools, including vulnerability scanners, SAST, and Security rating services, often lag behind in terms of accuracy, frequency, and scalability.
These tests may foster a false sense of security, as they frequently overlook comprehensive coverage of the entire attack surface. Moreover, the manual nature of penetration testing can lead to delays and limited scalability, posing challenges in keeping abreast of the rapid rate of exploit development.
To address these deficiencies, you must adopt automated solutions offering continuous exposure management. By harnessing AI-driven tools like Hadrian, penetration testers can augment their capabilities, remaining ahead of emerging threats and ensuring thorough coverage of the attack surface. Transitioning from reliance on legacy tools to proactive defence strategies is imperative to effectively mitigate the evolving risks of cyber attacks.
While traditional penetration testing remains vital for thorough examination of critical infrastructure, it is evident that the swiftly evolving cyber threat landscape necessitates a more adaptive and proactive approach. Automated testing, such as continuous exposure management, is indispensable for bridging the gap in assessments and guaranteeing exhaustive scrutiny of vulnerabilities across every facet of the attack surface.
Penetration testers must adapt their methodologies and embrace AI-driven solutions like Hadrian to stay ahead of emerging threats. It is time to pivot from reactive to proactive defence strategies, ensuring you remain resilient in the face of evolving cyber threats.
Push Button Pentesting
Push Button Pentesting (PBP) marks a significant evolution in penetration testing practice, offering a dynamic and efficient alternative blending of several critical components - vulnerability scanning, simulated attacks, social engineering and comprehensive reporting - into a cohesive ongoing sequential process.
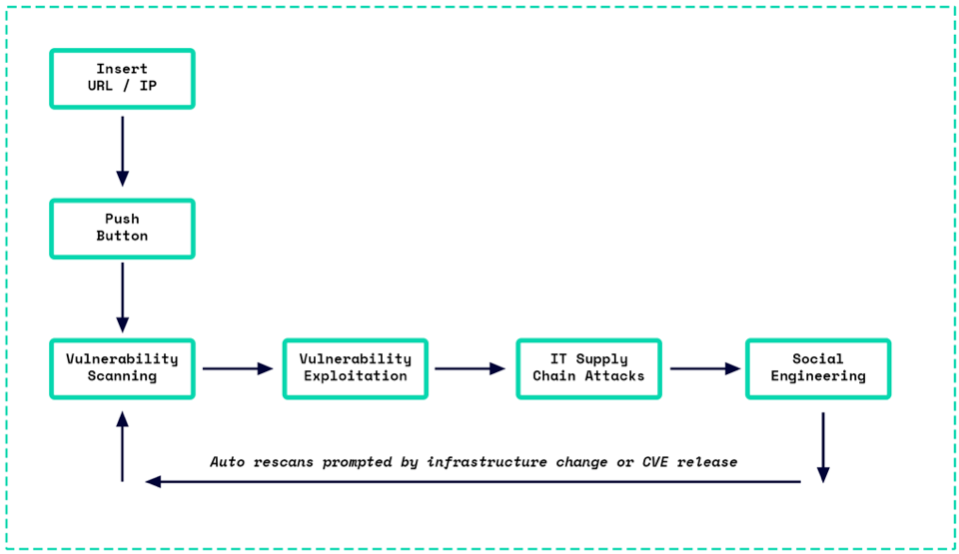
At its core, PBP automates and perpetuates the cycle of identifying and addressing security weaknesses within an organisation’s digital infrastructure. PBP brings important advantages for its users, including:
🔎 Identification of vulnerabilities in real-time; the ongoing process not only ensures comprehensive coverage of the entire network and system infrastructure but also brings consistency and standardisation to the testing process.
💶 Automation brings cost-efficiencies; it reduces the need for frequent manual testing, which can be resource-intensive and, by minimising human intervention, PBP lowers the risk of errors that can occur in manual processes.
📈 Scalability; as organisations grow and their network infrastructures become more complex, PBP adapts accordingly through fingerprinting, ensuring that new infrastructure components are continually assessed for vulnerabilities.
📋 Compliance; many industries are governed by regulations that mandate regular security assessments. PBP streamlines this process, making it easier for organisations to adhere to these requirements consistently.
About Hackurity
Hackurity is redesigning cybersecurity through its unique and innovative concept of Push Button Pentesting. By fully automating the discovery and exploitation of vulnerabilities, Hackurity is that all-important extra pair of hands for your IT team, contextualising risks in a unified repository, streamlining remediation.
Headquartered in the Netherlands and developed by pentesters, Hackurity provides enterprise security solutions to businesses around the world, small and large.