
Penetration testing and vulnerability scanning often are confused for the same service. In addition, the problem is that businesses often use one when they need to use the other. In this blog we’ll explain the differences between penetration testing and vulnerability scanning.
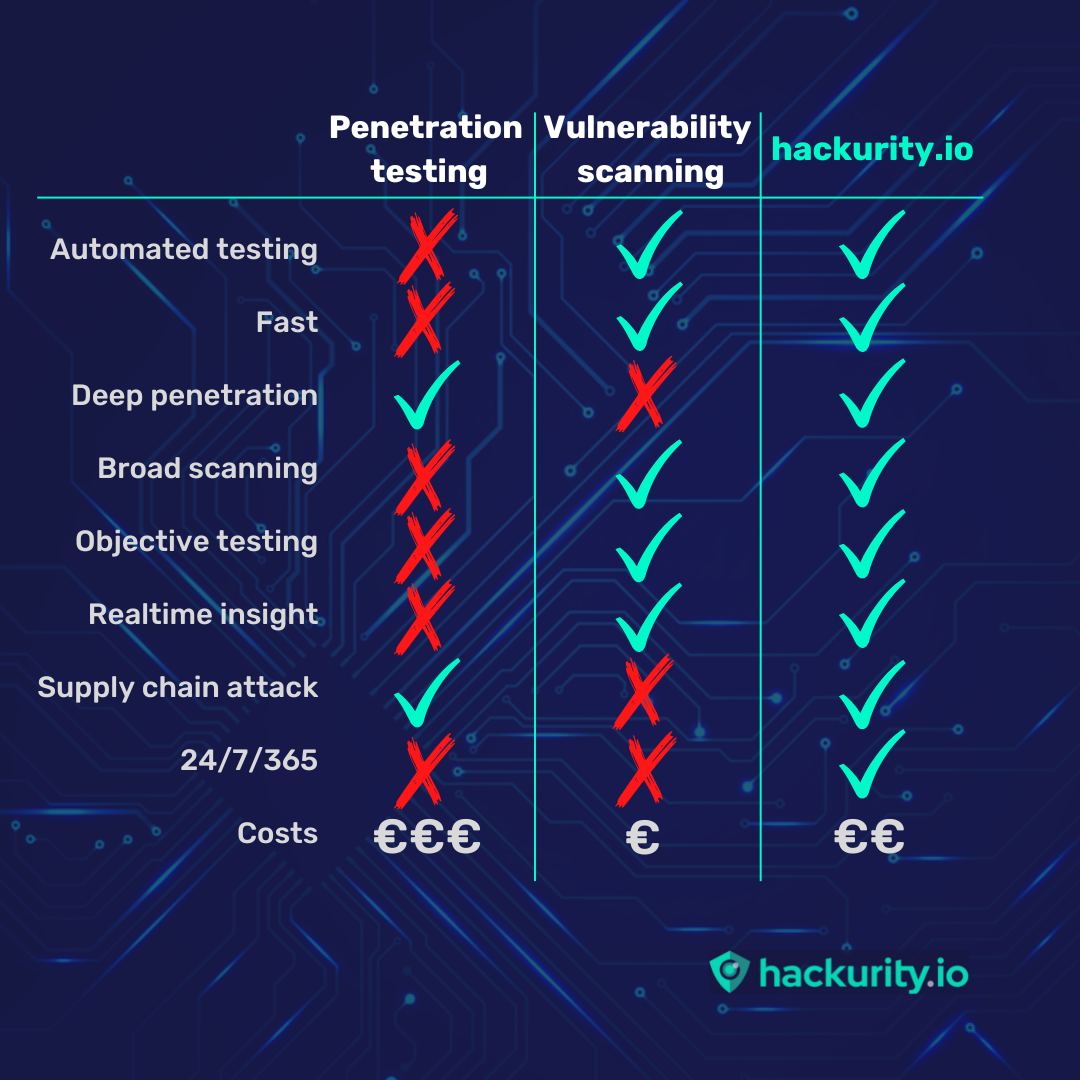
Penetration testing and vulnerability scanning are frequently confused, and it’s easy to see why. Both solutions search for weaknesses in your IT infrastructure by exploring it in the same way hackers would. They are different and have limitations. That is why at hackurity.io we are redefining these solutions with a whole new approach. Let's explore all options in more depth.
A deep dive into penetration testing
Penetration testing is a manual security assessment where a penetration tester tests your cybersecurity by attempting to breach your IT infrastructure. It’s a hands-on and in-depth security test which is conducted by cyber security specialist(s), often so called ethical hackers.
Simply said, a penetration test is an in-depth security test covering IT systems, applications, web and cloud environments and designed to evaluate cyber security measures and expose weaknesses in its defence against hackers. It’s in essence a full scale hacking attack on your business, with the difference being that it’s done by the good guys you hired.
Penetration testers will use similar tools, software, applications and skills as real hackers would do to find and exploit vulnerabilities in the IT infrastructure within your organisation. This includes, but is not limited to:
- Phishing attacks
- Social engineering attempts
- Hacking secured servers
- Hacking your website
- Detecting logic flaws
- Password & wireless network attacks
After the penetration test is concluded, the tester(s) create a full report containing a description methodology, all its findings and results and recommendations for enhancing your cyber security.
Penetration tests can take anywhere from one day to several weeks, depending on the how complex the IT infrastructure is and which systems are targeted by the penetration test. Due to the complexity of such tests, costs become quite staggering. For high quality penetration tests covering your complete IT infrastructure, costs often run up and even beyond $ 10,000 quite easily.
Penetration tests are typically run either bi-annually or annually, depending on the size of the organisation and the sensitivity of the data it holds. It provides valuable insight into existing vulnerabilities within the organisation and IT infrastructure and how they can be mitigated.
Performing periodical penetration tests has long been a cornerstone of cybersecurity measures for many organisations as protective measure against cyber threats. Based on the previous paragraphs you can see why. However, there are multiple downsides of relying on penetration testing. Let us explain.
What happens between the penetration tests? If you conclude a penetration test today, the result can already be outdated by tomorrow. What happens if a new, critical vulnerability is discovered in the Apache web server operating the sensitive data of your customer portal. That wouldn’t be discovered until the next penetration test, while it is a critical vulnerability exploitable by threat actors. Or what if a developer opens up a port?
How would these issues be discovered, who’s responsible for that and how long would it take? The longer it takes, the greater the chance of threat actors finding and exploiting them. A penetration test is always a snapshot of your cyber security.
Another weak point of penetration tests is that they rely on humans. Cybersecurity covers a wide range of systems, applications, etc., therefore it’s near impossible for anyone to be an expert in everything. This leads to, what we call, blind spots. These are aspects of cybersecurity that may be missed during a penetration test due to the expertise of the tester. Ultimately, this can create inaccuracies or incomplete penetration tests and reports without the tester or organisation realising and ultimately leading to vulnerabilities being missed.
Continuing on the weak spots of human penetration testers, they all rely on their intuition. Automated tools cover everything and are programmed to extensively tried and tested and updated. Human penetration testers execute the test, although based initial protocols, on their instincts, intuition and experience. Again, this means that certain areas of your IT infrastructure may be missed or skipped and leaving vulnerabilities undetected.
A deep dive into vulnerability scanning
Vulnerability scanning is automated process of proactively identifying network, application, and security vulnerabilities. The scanning process includes detecting and classifying system weaknesses in networks, communications equipment, and computers.
A vulnerability scanner uses a single or multiple databases to compare details about the target attack IT infrastructure. These databases reference known flaws, coding bugs, packet construction anomalies, default configurations, and potential paths to sensitive data that can be exploited by attackers. By using databases with known vulnerabilities, the human intuition and blind spots in expertise are removed, creating a better allround coverage of cyber security.
Because vulnerability scanning is an automated process, it’s running 8 to 16 hours per day and therefore always provides realtime insights into your cybersecurity. This makes vulnerability scanning especially attractive for organisations where there is rapid deployment of changes across their IT infrastructure.
Thanks to automated processes and tools, vulnerability scanning is cheaper than penetration testing. It can be run by your own IT team, but it is also possible to opt for specialised 3rd party cyber security partners.
Vulnerability scanners run hundreds or even thousands of security checks across your IT infrastructure, including your network, applications and systems. At the end of every full scan of the IT infrastructure targeted, the vulnerability scanner generates a report outlining all vulnerabilities found and the remediation for each.
Sounds like the perfect cybersecurity solution, right? Not quite so fast, as vulnerability scanning also has some disadvantages. Let’s look at the main ones.
Because vulnerability scanning is automated and focused on speed, its scanning is superficial compared to the in-depth penetration testing. It scans your IT infrastructure fast, based on vulnerability databases it tracks and only reports on any potential vulnerabilities it finds.
Last but not least, vulnerability scanners often raise false flags in their reports. For a large part this is due to the difference of intent between a vulnerability scanner and penetration testing. Penetration testing has the intent to actively exploit any vulnerability found. A vulnerability scanner just reports them and therefore can see things as vulnerabilities, which may be covered further in the cyber security measures. Raising false flags can also occur due to the speed of scanning and the databases it tracks. As your IT team can never know in advance what a false flag is, and thus they need to spend time checking all reported vulnerabilities. If a vulnerability scanner frequently reports false flags, it will waste many hours of your IT team and harm their morale.

Based on all the pros and cons of penetration and vulnerability scanners it is not always clearcut what option is best for your organisation or when. There are insurers who are also demanding organisations implement both solutions before they can issue insurance. Therefore the question is, what should you choose. What if there was a solution that offers the best of both.
All-in-one solution redefining cyber security
The question is, can the benefits of penetration testing and vulnerability scanning be joined into an all-in-one solution. A solution that can go deep like a penetration test, yet as broad as vulnerability scanning and all fully automated.
In order to achieve that, the problem needs to be looked at from a different angle. It requires for the penetration testing solution to run in a constant recursive loop; first enumerating the given target, then trying to attack it based on the resulting information.
That is exactly what we’ve developed at hackurity.io, the perfect all-in-one solution which runs fully automated 24/7/365.
Through our solution, we replicate the process of a real threat actor or hacker and take the outside in approach. We do not require login details, internal agents or any other type of initial network access for our solution to work. We also aim to achieve consistency by planting reverse shell triggers and/or backdoors as part of our network enumeration.
Our solution scans your domain automatically and continuously. Once it finds vulnerabilities it will take two actions.
- It will, within minutes, automatically notify you of the most critical vulnerability found through email.
- It will actively exploit the vulnerability and progress in penetrating your IT infrastructure.
Once you’ve fixed the reported vulnerability, our solution will automatically notify you of new/other vulnerabilities found by order of how critical these are. Vulnerabilities are found as our all-in-one solution exploits every vulnerability it finds. It will attempt to gain access to the core of your IT infrastructure step by step, like peeling an onion layer by layer.
In addition to this, we have also built in new toolsets to create firewall bypasses. Firewalls are an essential corner stone of cybersecurity. They can keep amateur hackers out, but professionals often are able to get around them. That’s why we have built into our solution tools to bypass firewalls, keeping up with the skills and tools threat actors develop for their criminal purposes.
Technically our solution runs as a lambda and it's in a constant recursive loop; first enumerating the given target, then trying to attack it based on the resulting information. If it succeeds it then goes back to enumerating using the newly gained access or information. This loop goes on until a viable compromise vector is found. Depending on the size of the loop this can be one or more vulnerabilities chained together.
We differentiate our solution further by aggregating several vulnerability databases, as well as adversary simulation frameworks. This in effect ensures that we can target our customers with new CVEs as soon as they get their attack vector or exploit POC assigned. This is weeks before the public media or news sites pick up the new CVEs, which happens only after a high profile target is compromised.
About hackurity.io
Hackurity.io is redefining cybersecurity through our innovative, automated and powerful cybersecurity and attack simulation tools. Taking a unique outside in approach, our solutions are designed to replicate real hacker attacks to find and fix vulnerabilities before hackers do. Focused on prevention, we reduce the chance of a successful cyber attack on any business by up to 95%
Founded in 2021, hackurity.io has the dream and mission to make being connected to the internet safer for all businesses and ultimately for our next generations. Headquartered in The Netherlands, hackurity.io offers its world class cybersecurity solutions to businesses around the world.
You can book your free trial now: hackurity.io/contact or harold@hackurity.io