
Automation is nothing new and implemented within most organisations across multiple functions. Recent statistics indicate that 31% of businesses have fully automated at least one function. Automation has become an essential part of most business functions, whether it be marketing, data entry, finance or something else. However, automation isn’t used as often as it can be within the field of penetration testing.
What is pentesting?
Penetration testing is traditionally a manualsecurity assessment where a penetration tester tests your cyber security by attempting to breach your IT infrastructure. It’s a hands-on and in-depth test which is conducted by cyber security specialist(s), often called ethical hackers.
Simply said, a penetration test is an in-depth security test covering IT systems, applications, web and cloud environments and designed to evaluate cyber security measures and expose weaknesses in its defence against hackers. It’s in essence a full scale hacking attack on your business, with the difference being that it’s done by the good guys you hired.
Penetration testers will use similar tools, software, applications and skills as real hackers would do to find and exploit vulnerabilities in the IT infrastructure within your organisation. This includes, but is not limited to:
✅ Phishing attacks
✅ Social engineering attempts
✅ Hacking secured servers
✅ Hacking your website
✅ Detecting logic flaws
✅ Password & wireless network attacks
After the penetration test is concluded, the tester(s) create a full report containing a description methodology, all its findings and results and recommendations for enhancing your cyber security.
Penetration tests can take anywhere from one day to several weeks, depending on the how complex the IT infrastructure is and which systems are targeted by the penetration test. Due to the complexity of such tests, costs become quite staggering. For high quality penetration tests covering your complete IT infrastructure, costs often run up and even beyond $ 10,000 quite easily.
Penetration tests are typically run either bi-annually or annually, depending on the size of the organisation and the sensitivity of the data it holds. It provides valuable insight into existing vulnerabilities within the organisation and IT infrastructure and how they can be mitigated.
The benefits of penetration testing
The main benefit of penetration testing is that it provides you with visibility into any holes or vulnerabilities in your current security posture and to find them before threat actors can exploit them. This includes both known and unknown, or zero-day, vulnerabilities.
Another advantage is how penetration testing takes the hacker’s mindset. It replicates how threat actors would utilise their tactics and techniques when attacking your business. This creates important insights what digital assets will be targeted during a real attack.
The main downside of penetration testing is that it’s not a continuous testing tool, meaning that between scheduled tests your business may remain vulnerable to exploits.
Automating your security testing
As the number and variety of cyberattack exploits available today reinforce the need for penetration testing to be as comprehensive as possible. One way of achieving this is through testing all areas of your technology stack. For example, you should employ website pen testing on your public-facing digital assets, where pen testers focus on hidden vulnerabilities and common attack patterns that target internet assets.
Other forms of testing include network pen testing, cloud pen testing, API pen testing, end point pen testing and many more. However, for a comprehensive defence, automated penetration testing is more effective, and reduced drain on resources, than manually testing your entire attack surface.
Automated penetration testing utilises software and algorithms to eliminate manual processes that are used in traditional manual testing. With automated pen testing, 24/7 vulnerability scanning is employed eliminating the need for manual testing of assets. This greatly speeds up the process of risk identification and remediation.
The benefits of automated penetration testing extend well beyond speed and efficiency. It’s also highly cost-effective and using Hackurity’s platform, comprehensive security and compliance reports can be generated with a single click. The resource savings you’ll get with automated penetration testing are early due to the recent advances and implementation of artificial intelligence (AI) technology. Utilising AI within Hackurity’s solutions, its automated pen testing is improving daily in speed, capabilities and cost-efficiency.
Like the promise of discovering increasingly advanced and complex exploits, automated penetration testing also takes on mundane and repetitive tasks from your team. As parts of security testing can be executed by automation, your security team can focus on adding value through faster remediation.
Find exploitable risks before threat actors do
Through our experience, we notice that businesses are adopting automation to improve their penetration testing. The pace at which cyberattacker and cybercriminals are moving means that periodic testing or time-consuming manual tasks are no longer fit for purpose. Instead, you need to be able to uncover vulnerabilities as soon as they appear.
Automation is also increasingly used by cybercriminals themselves, hence the argument to implement it to aid your security posture and cyber defences. The workload of IT security staff is high and will only increase. Automated penetration testing streamlines workflows for your security team, it’s not meant to replace them.
With Hackurity, automated pen testing continuously scans your entire attack surface to identify exploitable risks. New security tests are triggered immediately when changes to your infrastructure are detected which could affect your risk level. With Hackurity theere is no need to wait for your next manual test, our automated pen testing tests your attack surface 24/7/365.
Push Button Pentesting
Push Button Pentesting (PBP) marks a significant evolution in penetration testing practice, offering a dynamic and efficient alternative blending of several critical components - vulnerability scanning, simulated attacks, social engineering and comprehensive reporting - into a cohesive ongoing sequential process.
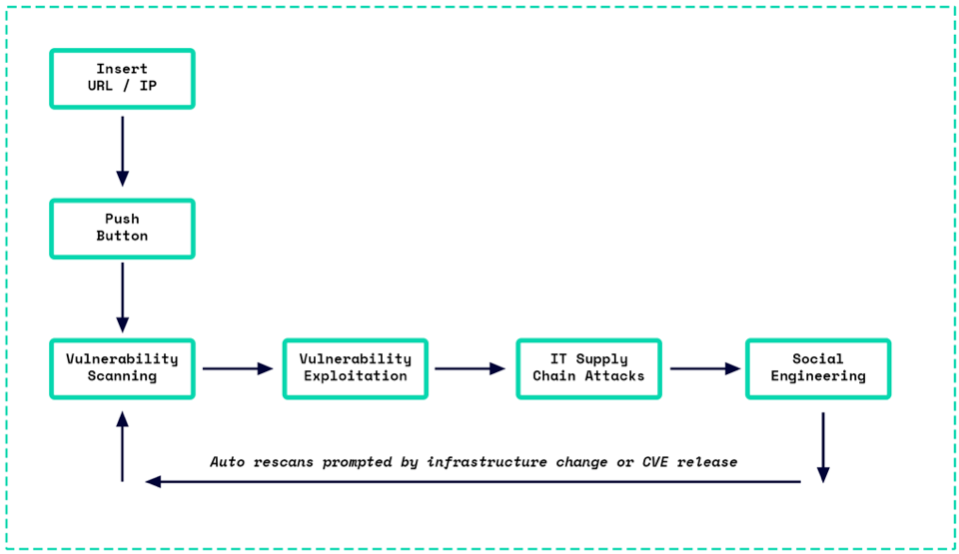
At its core, PBP automates and perpetuates the cycle of identifying and addressing security weaknesses within an organisation’s digital infrastructure. PBP brings important advantages for its users, including:
🔎 Identification of vulnerabilities in real-time; the ongoing process not only ensures comprehensive coverage of the entire network and system infrastructure but also brings consistency and standardisation to the testing process.
💶 Automation brings cost-efficiencies; it reduces the need for frequent manual testing, which can be resource-intensive and, by minimising human intervention, PBP lowers the risk of errors that can occur in manual processes.
📈 Scalability; as organisations grow and their network infrastructures become more complex, PBP adapts accordingly through fingerprinting, ensuring that new infrastructure components are continually assessed for vulnerabilities.
📋 Compliance; many industries are governed by regulations that mandate regular security assessments. PBP streamlines this process, making it easier for organisations to adhere to these requirements consistently.
About Hackurity
Hackurity is redesigning cybersecurity through its unique and innovative concept of push button pentesting. By fully automating the discovery and exploitation of vulnerabilities, Hackurity is the extra pair of hands for your IT team. Our auto reporting contextualises risks in a single dashboard, making remediation more efficient.
Developed by enterprise pen testers, Hackurity provides 24/7 security, focused on prevention. Headquartered in The Netherlands, hackurity.io offers its world class cybersecurity solutions to businesses around the world.